The 7 pillars of zero-trust security

Zero trust is a security model based on the assumption that threats exist both within and outside a system. In a zero-trust model, you trust no one until they’ve been adequately authenticated, and even then you grant verified users least-privilege access.
Zero-trust architecture is built on seven key pillars: user, device, data, application and workload, network and environment, automation and orchestration, and visibility and analytics. These pillars work together to ensure enhanced network security.
In this guide, we’ll explore the zero-trust security pillars in-depth, focusing on benefits, common implementation challenges, and how to achieve zero-trust program maturity.
Note: ExpressVPN is a consumer privacy service, not an enterprise security framework like zero-trust security. We cover this topic because it has become an influential framework in cybersecurity and an important part of the broader conversation on digital privacy.
Zero trust in one minute
Zero trust is a cybersecurity approach that operates on the assumption that your network is already compromised, or it might as well be.
In a zero-trust system, every user, device, application, or other entity trying to access a network resource must first be verified to be who/what they say they are. Then, they must be continuously monitored for their security posture, based on which they’re granted or denied sustained network access.
This differs from traditional perimeter-based security systems, which rely on the principle that only those outside a system can be hostile, while everyone inside the system is trusted.
The zero-trust security model ensures that a valid means of primary authentication alone (such as a username and password) doesn’t grant users access to every part of a system. This least-privilege access makes it challenging for a malicious insider or network intruder to move laterally across a network from a single point of entry.
The 7 pillars of zero trust explained
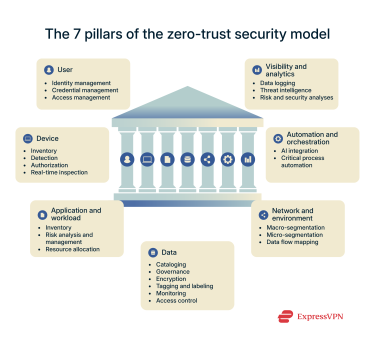
The U.S. Department of Defense (DoD) developed the seven zero-trust pillars based on the foundational research done by the National Institute of Standards and Technology (NIST). NIST’s research (NIST Special Publication 800-207) defines the core zero-trust principles, including least privilege, assuming a breach, and continuous verification.
Below is an in-depth description of each pillar of the zero-trust framework.
1. User
The user pillar ensures no single user is implicitly trusted. Instead, continuous authentication must be enforced to verify that the user is (and remains) who they say they are, while also defining the network resources they can access based on security policy parameters.
According to the 2025 Verizon data breach investigations report, 22% of known entry points for cyberattacks were from credential abuse. Phishing attacks accounted for another 16%, showing how employee and authorized user vulnerability could compromise network security.
To tackle these issues, the user pillar is built upon:
- Identity management: Helps manage legitimate users on the network through the following methods:
- Audit: Get a list of all users who have access to network resources.
- Review: Review the privileges of users with access to network resources.
- Manage: Remove users who no longer need access to resources (ex-employees, former contractors, etc.).
- Streamline: Gather information in a centralized database to keep identity information and clearances updated and synced across the network.
- Credential management: Securely maps access credentials to each user, allowing them to prove to the network that they are who they say they are. Here’s how:
- User provisioning: Each user (such as an employee, partner, or contractor) gets access credentials (username and password, etc.).
- Privilege definition: For instance, role-based credentials that may grant an employee access to basic everyday expense sheets but not the global financial documents.
- Layered security: Uses multi-factor authentication (MFA) to strengthen user verification.
- Access management: Defines who has access to certain system resources. Here’s how:
- Least privilege: Grant everyone on your network the least access they need to complete their tasks.
- Ongoing reviews: Regularly review user access to ensure no user has sustained access to resources they no longer need.
- Introduce automation: Automate your systems to revoke access based on certain triggers (such as cross-departmental promotions, retirements, job changes, etc.).
- Time-based access: Set up user access to certain systems for only a predetermined period.
2. Device
The device pillar ensures every device connecting to a zero-trust network is identified, assessed for its security posture, and authenticated before it gets network access.
The National Security Agency (NSA) defined a useful roadmap for ensuring device security in a zero-trust strategy, as outlined below:
- Device inventory: Gather information on all existing devices on your network. That helps define policies for these devices, identify risks, and block unauthorized devices from your network.
- Device detection and compliance: Existing and new devices on a network should be continually monitored to ensure compliance with policy guidelines. A policy that calls for post-quantum encryption, for instance, means older devices that can’t use this encryption shouldn’t be granted network access or should only be given limited access.
- Device authorization with real-time inspection: Devices should be re-checked, re-verified, and re-authorized for access to critical resources based on real-time inspection and security posture assessment, not on a history of being granted access in the past.
- Remote access protection: Where remote or hybrid access is permitted, the device pillar policies still apply without exceptions.
- Automated vulnerability and patch management: Device firmware, software, and operating system vulnerabilities increase the likelihood of breaches. The device pillar policy may include automated device and software updates to ensure continuous compliance.
- Centralized device management: Maintaining a centralized access console for all devices offers improved device overview (including health tracking) and management. It also helps network analysts generate data for relevant analytics.
- Endpoint threat detection and response: Devices should be equipped with capabilities, such as firewalls and anti-malware solutions, for local threat detection and management.
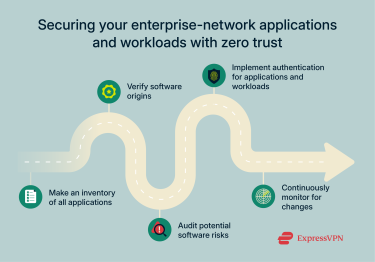
3. Application and workload
Applications refer to the programs and software running on your network, whereas workloads are the tasks performed by these applications.
Here’s how the zero-trust approach secures your applications and workloads:
- Application inventory:
- Audit and inventory all applications and workloads currently running on your system or network.
- Remove unapproved or unused applications to reduce the potential attack surface.
- Secure software:
- Verify application software origins using its unique digital signatures or other cryptographic proof.
- Software risk management:
- Understand the potential risks that come with using each application.
- Constantly test to ensure the risks don’t outweigh the benefits.
- Limit access granted to each software application and workload, preventing cybercriminals or malicious insiders from moving laterally across the system.
- Resource authorization and integration:
- Consider granting applications and workloads unique authentication credentials to access critical system resources.
- Remove software access once it’s no longer needed on the network.
- Continuous monitoring and ongoing authorizations:
- Always monitor for changes that may introduce vulnerabilities into software and workloads or mimic secure application access.
- Set up dashboards and alerts that instantly notify you of critical changes, concerns, or vulnerabilities in the application software and workloads.
4.Data
The data pillar is concerned with the proper handling, management, storage, and encryption of organizational data at rest or in transit. Beyond enterprise data protection, the data pillar’s provisions can also help you stay compliant with applicable data laws, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA).
Here’s how the zero-trust data pillar makes that happen:
- Data cataloging: All data within an organization should be identified, cataloged, and assessed based on sensitivity and risk of exposure.
- Data governance: Data security policies should be established to define who can access what data, for how long, how the data should be stored, managed, or shared, and other considerations.
- Data labeling and tagging: Labels and tags help an enterprise quickly manage large datasets, automating assignment to authorized users and assessing risks.
- Data monitoring: Helps maintain an overview of what data has been accessed, shared, modified, or used in any way (and by whom).
- Data encryption and rights management: Ensures continuous data privacy and security, even if the data is stolen or exfiltrated by a malicious actor. After all, strong data encryption methods (for data at rest and in transit) are practically unhackable for threat actors.
- Data loss prevention: Prevents data leakages, corruption, and losses by blocking unauthorized exfiltration or destruction attempts.
- Data access control: Defines which users and devices have access to certain data. Adaptive role-based access control or session-based access controls can be deployed here.
5. Network and environment
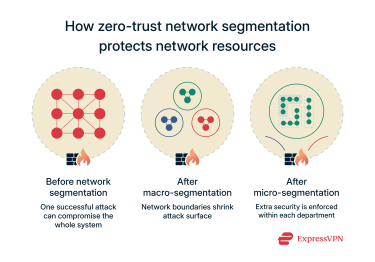
In a perimeter-based security system, anyone within the perimeter (including threat actors) is granted broad access to critical and sensitive resources within the network. The zero-trust model takes a different approach and addresses network and environment vulnerabilities by doing the following:
- Data flow mapping: Locates the routes through which data flows in your organization, exposing any unencrypted data flow paths.
- Macro-segmentation: Breaks down the network into major segments and defines data flow and access controls for each segment. In practical terms, think of it as having different network segments for employees in different departments (such as engineering and finance).
- Micro-segmentation: Offers even more granular network segmentation to prevent data leaks within the same macro-segment. So, for example, two employees in different roles within the engineering department don’t have explicit access to one another’s network resources and data.
- Software-defined networking (SDN): Organizations can configure SDN tools to automate and reduce human error in micro- and macro-segmentations. SDN is also useful to handle rapidly growing teams, adapt to network changes, and segment new users and devices correctly while still offering improved network visibility.
6. Automation and orchestration
Automation plays a significant role in zero-trust systems, but it isn’t a set-and-forget solution; automated systems should be constantly audited to ensure they’re not susceptible to new or existing manipulations.
Here’s how you can implement automation in line with zero-trust security principles:
- Policy orchestration: Zero-trust policies should be developed and maintained in machine-readable formats. This allows automated systems to access this information and interpret it for improved network security and compliance.
- Critical process automation: Critical (and often repetitive) processes such as granting user access, enforcing network security policies, and assigning network access based on user or device type can be automated. This reduces human error and boosts operational efficiency while improving the security landscape.
- AI integration: AI tools can collect, track, and comb through large datasets faster than human employees. However, human oversight is still needed to keep the AI on the right track.
- Machine learning (ML) adoption: ML allows companies to train models based on internal data and arrive at meaningful conclusions. It can be used to map patterns (such as tags and labels) to actions (such as user provisioning and access control), further boosting efficiency and reducing human error.
- Security orchestration, automation, and response (SOAR): SOAR combines AI and ML capabilities with internally developed policies for faster incident response, improved logical insights based on collected data, and better identification of anomalous behavior.
- Data exchange standardization: Interoperability between systems, services, and applications is key for a more streamlined security model. With standardized data exchange methods, solutions can be built and deployed on the entire network rather than dealing with the added complexity of building for each network subset.
- Security operations coordination (SOC): SOC collects automated data and logs, constantly analyzing them and drawing from logic to improve threat detection, response, and mitigation.
7. Visibility and analytics
The visibility and analytics pillar involves logging and collecting data on system health, status, threat insights, and component behavior. These insights can be used to improve the zero-trust security policy, create a game plan to better anticipate and tackle threats, and maintain a comprehensive picture of the system’s strengths and weaknesses.
This pillar of the zero-trust system includes:
- Data logging: Data from all network devices (routers, switches, etc.), users and their devices (operating systems, applications, etc.), authentication services, and other resources should be mapped, identified, and collected.
- Centralized security information and event management (SIEM): SIEM aggregates collected data, draws actionable insights from it, and provides insights in clear dashboards for easy decision-making.
- Analyzing risk and security: Assigns risk factors to the data and other resources on the network based on the implemented security measures and criticality of network assets.
- Analyzing user and entity behavior: Using AI and ML, user behavior should be analyzed for anomalies consistent with a malicious insider or breached credentials.
- Integrated threat intelligence: Improves your threat awareness with reliable outside threat analytics and detection data. This keeps you ahead of the curve on threats that haven’t affected you but already exist in the wild.
- Dynamic policy automation: Leverage AI and ML to adapt your network security posture based on a changing security landscape.
The benefits of zero trust
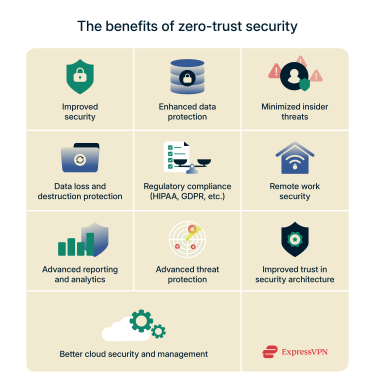 Zero trust can be complex and expensive, especially for networks transitioning from a traditional security model. However, making this switch comes with many benefits, including:
Zero trust can be complex and expensive, especially for networks transitioning from a traditional security model. However, making this switch comes with many benefits, including:
- Improved security: By assuming nobody can be trusted, you reduce the chances of suffering a severe data breach.
- Enhanced data protection: Zero-trust security enforces data encryption (in transit and at rest). Exploring post-quantum data encryption technologies also keeps sensitive data secure far into the future.
- Minimized insider threats: Zero trust’s restriction of lateral movement within a network minimizes the impact of insider threats. Combined with data encryption during exfiltration, malicious insiders will face more challenges if trying to steal sensitive data.
- Data loss and destruction protection: Zero trust instills safeguards preventing threat actors from destroying or corrupting data on your systems.
- Better regulatory compliance: Zero trust helps to ensure compliance with data protection legislation by preventing data loss or mismanagement.
- Better remote work security: It improves how network resources are accessed by users and devices that are not on-site and therefore not protected by traditional perimeter-based security.
- Advanced reporting and analytics: With zero trust, you can focus your IT talent on advanced tasks and implementations. After all, integrated AI and ML systems can now help with data collection, policy implementation, and anomaly tracking.
- Protection against new cyberthreats: Zero trust’s AI and ML integration can help you detect threats you’d have missed if you were using traditional security systems.
- User convenience: A well-designed zero-trust model supports single sign-on (SSO), which brings all the network assets a user needs under one umbrella. This prevents multiple authentication roadblocks while still enforcing least-access privileges.
- Improved trust in security architecture: Zero trust removes the guesswork by giving you a better overview of your network and its components, health status, and risk profile.
- Better cloud security and management: Organizations often depend on their cloud provider’s security model since they can’t apply perimeter-based access to something that’s not on-premises. Zero trust takes care of that, since it classifies all data assets (including cloud data) into its overall framework.
Overcoming common implementation challenges
Implementing zero-trust network architecture (ZTNA) can come with some challenges, including:
- Migration from legacy security systems: Consider a gradual switch, which begins by auditing your resources to identify the most at-risk and sensitive data.
- High upfront costs: You may need to change network devices (such as servers), user devices (such as desktops), and other devices to ensure zero-trust compatibility. That’s not considering extra spending on AI and ML if you don’t already have those systems set up. Considering that the average cost of an insider-driven breach is nearly $5 million, though, the cost of migration is justified.
- AI and ML capabilities: AI and ML are fast-evolving technology fields, and the right expertise may be challenging to find. You may consider working with a trustworthy third-party vendor rather than setting up an in-house team right away.
- Mapping data sources: Still on AI and ML, the zero-trust architecture must be fed with clear and relevant data to help it understand your network enough to make decisions. This is challenging if you don’t have properly mapped data sources. Here, you can start with a small, sensitive data set, then work your way up into the rest of the system.
- Managing permissions: Managing user permissions correctly is a key challenge. Start by mapping network devices and users to the core resources they need to complete their tasks. Tags and labels are useful to help you automate the process.
- Reducing operational fatigue: Employees, partners, and anyone else on your network might get frustrated if they have to constantly re-verify their credentials to access different parts of your network. To tackle this, consider implementing SSO or other frictionless and user-friendly methods.
- Third-party risk management: Most organizations don’t develop their zero-trust systems from scratch, instead preferring to contract third-party vendors. While this helps save costs, you should be careful not to open yourself up to new breaches due to vulnerabilities in the vendor’s model.
How the pillars interact in real environments
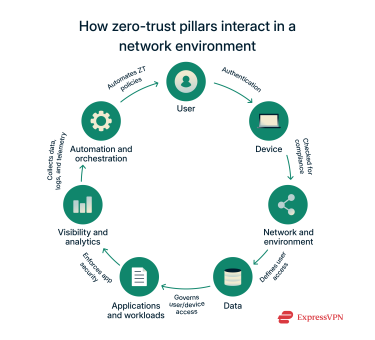 Zero-trust pillars are designed to interact to deliver a seamless user experience while maintaining a healthy security profile.
Zero-trust pillars are designed to interact to deliver a seamless user experience while maintaining a healthy security profile.
For example, let’s consider an employee, Bob, who wants to access his organization’s inventory spreadsheet to create the next month’s forecast:
- User pillar: Bob logs into the company’s network with his access credentials, confirming his identity. Bob also has to use MFA to access sensitive parts of the inventory document, such as vendor data.
Why did Bob need to use MFA? In case someone else is trying to use his credentials to gain access.
- Device and automation pillars: Bob might be prompted to update his system applications or operating system to the latest version before continuing to the desired spreadsheet.
Why did Bob need to update his system and apps? In case there’s a vulnerability in the older versions that attackers could exploit.
- Network and environment pillar: Due to macro-segmentation, Bob can’t pull up spreadsheets from the finance department to see how much the company spent on its inventory from the last quarter.
Why was Bob blocked from accessing finance data? To ensure that employees can only interact with the parts of the network relevant to their role, limiting lateral movement in case of a compromise.
- Application and workload pillar: Since Bob’s department doesn’t usually handle the financials, he has to request access from the finance department to get the specific data he needs from their network.
Why does Bob need to request access? To enforce least-privilege principles, access is only granted when necessary and justifiable, reducing the risk of over-privileged users.
- Data pillar: Bob tries to copy the data onto his flash drive to continue working on the file from home, but the system blocks such exfiltration.
Why was Bob blocked from copying the data? To protect sensitive information from unauthorized transfer or leakage, especially onto unsecured or unmanaged devices.
- Automation pillar: The blocked data exfil didn’t need to be initiated manually. Rather, it was automatically triggered by policy baked into the system.
Why was automation used? To ensure quick, consistent enforcement of security policies without relying on manual intervention.
- Visibility and analytics pillar: Bob’s login, movement within system resources, request for access, and attempt at data exfil were logged by the system.
Why was all this logged? To detect unusual behavior, investigate incidents, and ensure compliance.
Overall, all the pillars worked together to allow Bob just the right access he needs, block him from areas where he shouldn’t have access, and prevent data loss or leaks.
From pillar focus to program maturity
The Cybersecurity and Infrastructure Security Agency (CISA) developed a zero-trust program maturity roadmap, which compresses the pillars from seven to five:
- Identity
- Devices
- Networks
- Applications and workloads
- Data
This roadmap helps organizations move from viewing ZTNA as an abstract concept to full implementation. There are 4 stages to this journey:
Stage 1: Traditional
The start of your implementation is characterized by the following:
- Zero-trust lifecycles are configured manually.
- Attributes such as security and logging are assigned manually.
- Security policies and solutions are static and mapped to one pillar at a time.
- Least privilege is manually configured at the point of creating, managing, or deleting user accounts.
- Threat response and mitigation efforts are deployed manually.
- Policy enforcement is restricted within individual pillars.
- Dependencies, logs, and telemetry don’t fully correlate at this stage.
Stage 2: Initial
The system develops, notably to include automation:
- Automation is introduced into processes such as the assignment of attributes (e.g., user identity).
- Responsive changes to least privilege after user provisioning (account creation, management, and deletion) are introduced.
- Improved visibility for internal systems.
- Development of cross-pillar solutions.
Stage 3: Advanced
Automation continues to advance, and the pillars now start functioning together:
- Centralized dashboard for improved visibility and identity management.
- Automated response to predefined instances.
- Cross-pillar policy enforcement.
- Steps toward enterprise-wide coverage and zero-trust solutions.
- Least privilege changes based on risk posture and assessment.
Stage 4: Optimal
Here’s the ultimate goal of ZTNA:
- Achievement of a fully automated, self-reporting system.
- Dynamic least privileges for assets and enterprise-wide dependencies.
- Cross-pillar interoperability.
- Improved centralized dashboards and overall visibility console.
- Dynamic policies for automatic implementation based on automated or observed triggers.
FAQ: Common questions about zero-trust pillars
Do I need to implement all seven pillars at once?
You don’t need to implement all seven pillars of the zero-trust security model at once. Instead, audit your current security model and gaps, then start with the pillars that help secure your highest-risk data first. Ultimately, you should aim to implement all seven pillars to ensure highly functioning network security.
Which pillar is the best starting point for SMEs?
The user pillar is an excellent zero-trust starting point for small and medium-sized enterprises (SMEs), ensuring tightened user verification protocols before network access and least privilege after access. This keeps SMEs from being breached by unauthorized users or being targeted as a weak point to breach a larger organization.
What is the NIST zero-trust architecture?
The National Institute of Standards and Technology (NIST)’s zero-trust architecture builds on the seven key pillars of zero trust by defining what devices are on a network, specifying how communications should be treated, and stressing the re-verification of users and devices before accessing network resources. It also supports least privilege, promotes dynamic policy setups, and encourages data collection for threat monitoring and rapid threat response.
What is the DoD zero-trust reference architecture?
The DoD zero-trust reference architecture is a strategic framework published by the U.S. Department of Defense to guide how military and defense organizations should implement zero-trust security principles across their networks, systems, and operations.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN